Blockchain security audit services
Enhance your blockchain project's security with our specialized audit services. We meticulously assess every layer of your infrastructure, identifying vulnerabilities and validating security protocols to safeguard against emerging threats.
Secure Your Project with Expert Audit and Testing Services
Code
Code analysis and code review
Our code review service caters to projects with incomplete code, offering recommendations for code assurance and a comprehensive to-do list for subsequent audits. We ensure robust blockchain security through thorough analysis and guidance for projects in early development stages.
Gas
Gas usage optimization
Safeguard your token ecosystem with our comprehensive audit services. Our expert team meticulously reviews contract code for vulnerabilities, assesses economic models, verifies compliance with token standards, and provides actionable recommendations to bolster security and trust.
PT
Penetration testing
Conduct thorough security assessments through our penetration testing services. We identify and exploit vulnerabilities, enhancing your system's resilience against potential threats. Receive detailed reports for improved security.
Load testing
Assess the reliability and scalability of your software with our load testing services. We simulate user activity to identify performance bottlenecks, ensuring smooth operation even at peak loads. Partner with us to optimize your software's performance.
“Our mission is to empower businesses with the confidence to innovate fearlessly in the blockchain space. Through rigorous auditing, we pave the way for secure and sustainable growth in the decentralized landscape.”

Dan E. CEO | Rock’n’Block
Blockchain Projects We've Crafted
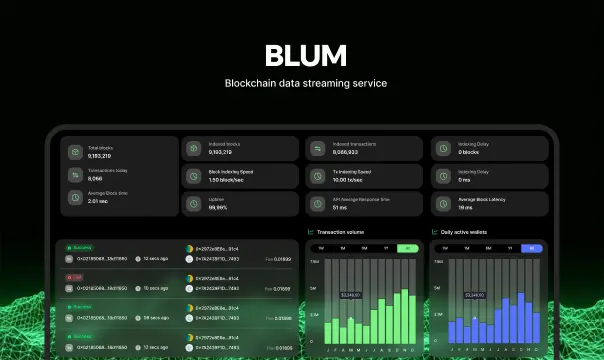
We helped Blum implement a Firehose/Substreams indexing stack that delivers 10k+ RPS, low-latency streaming, parallel historical processing, and stable reorg handling for their 65M-user multi-chain platform.
Tech Stack:
Go
Rust
See more

SwapX partnered with our team to build a ve(3,3) DEX on Sonic, with AMM and CLMM integrated with ICHI for automated liquidity, a Voting Escrow and rewards system, and over 30 interconnected smart contracts tied together with backend and frontend.
Tech Stack:
Solidity
GraphQL
React
Python
Typescript
See more
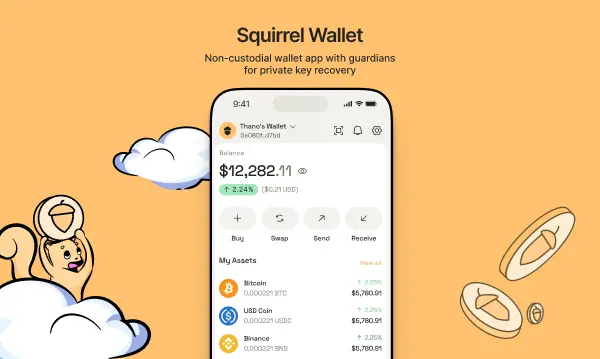
We helped Squirrel Wallet deliver a self-custodial mobile crypto wallet with on-device key management, social recovery via Guardians using sharded secrets, and provider-agnostic rails for swaps and fiat on-ramps
Tech Stack:
Python
PostgresQL
Django
TypeScript
Solidity
React
See more

Delivered a Shibarium liquid staking platform with custom BONE→knBONE staking contracts, an Ethereum↔Shibarium bridge, and full farming and vesting modules
Tech Stack:
React
Redux
Material UI
Python
PostgreSQL
Django
Solidity
See more
Rocking Blockchain Expertise
6
Years Custom Blockchain Development
With over 15 years of dedicated involvement in blockchain development, our team has cultivated exceptional expertise, positioning us as a leading expert in creating blockchain games. Our deep understanding across diverse aspects of the field solidifies our reputation as a top-tier blockchain gaming app development company.
ANY
Blockchain Integration and Development
Backed by a robust team and extensive experience, we excel in conquering challenges and untangling complexities seamlessly. As an expert blockchain development company and your trusted Blockchain Development Partner, we specialize in uncovering solutions and executing tasks to create blockchain games of any nature.
150+
Blockchain Experts
Our dynamic team of 150+ blockchain development experts forms our core, proficient across a diverse tech stack, and well-equipped to address any blockchain game development challenge. Count on us as your dedicated Full-Stack Blockchain Development Company, driving innovation hand in hand to create blockchain games that captivate audiences.
1 Bn+
Dollars Capitalization of Projects
Our impact transcends solutions – it's about fostering growth. Projects we've built have achieved a capitalization of over 1 billion dollars, showcasing the importance of crafting scalable solutions that facilitate business expansion in the realm of blockchain gaming app development. Count on us to guide projects with expert insights and ignite growth effortlessly.
What our clients tell about us
Ducatus
When it comes to the development of our blockchain and smart contracts, we trust only those trusted by experts. Rock’N’Block, developers of the Ducatus wallet and the DucatusX blockchain, recognized by industry experts globally.
Apiz Token
Excitingly, APIZ excels in web3 integration, aided by our trusted partner Rock'n'Block Together, we are leading a smooth shift towards a decentralized, blockchain-driven future. Embracing Web3 unlocks innovative monetization and global market reach. Success entails conquering these challenges and embracing the decentralized paradigm.
“Our blockchain security auditing methodology is anchored in meticulous attention to detail. We leave no stone unturned in scrutinizing your system's infrastructure, smart contracts, and cryptographic protocols. By employing advanced testing techniques and leveraging industry best practices, we empower you to proactively mitigate risks and safeguard your digital assets against emerging threats.”


























%201.webp)



